Event-driven optical encryption advances information security through neuromorphic imaging
In an era where the internet connects virtually every aspect of our lives, the security of information systems has become paramount. Safeguarding critical databases containing private and commercial information presents a formidable challenge, driving researchers to explore advanced encryption techniques for enhanced protection.
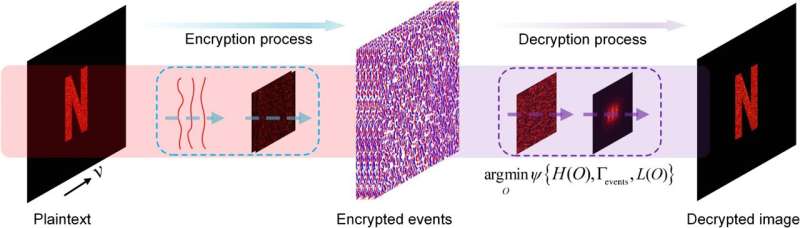
Data encryption, a cornerstone of modern security practices, transforms readable plaintext into encoded ciphertext, ensuring that only authorized recipients can decipher the data using a decryption key or password. Optical techniques have emerged as promising tools for encryption due to their capabilities for parallel, high-speed transmission, and low-power consumption. However, traditional optical encryption systems often suffer from vulnerabilities where plaintext-ciphertext forms remain identical, potentially compromising security.
Reporting in Advanced Photonics Nexus, scientists have unveiled an approach inspired by bio-inspired neuromorphic imaging and speckle correlography. Their innovative technique leverages computational neuromorphic imaging (CNI) to encrypt images into event-stream ciphertexts, marking a significant departure from conventional methods. This method introduces a new paradigm in optical encryption by converting data into event-driven formats, thereby significantly enhancing security and complexity.
Dr. Edmund Y. Lam, lead researcher of the study, elaborates, “Our methodology enhances speckle correlation through event-stream data, marking a transformative shift in optical image encryption. By integrating the CNI paradigm with random speckles, we achieve high-level information conversion that surpasses traditional encryption techniques.”
The proof-of-principle experiments conducted by the team demonstrate the feasibility and efficacy of their approach. Unlike previous methods, which required complex setups and consumed high computational power, the neuromorphic encryption technique offers a streamlined optical configuration with a sophisticated inverse scattering process. This not only strengthens security protocols but also facilitates high-speed data transmission—a critical advantage in today’s data-intensive environments.
“This is the first implementation of event-driven optical image encryption,” Lam notes. “Our solution harnesses the high temporal resolution, high pixel bandwidth, and low power consumption inherent in CNI techniques, paving the way for practical applications in information security.”
The implications of this research extend beyond encryption technologies alone. The integration of neuromorphic imaging principles into optical systems not only enhances data security but also holds promise for advancements in biomedical imaging, remote sensing, and autonomous technologies.
Despite the promising strides made, challenges remain in scaling and integrating neuromorphic encryption into broader applications. Nevertheless, the researchers are optimistic about the potential impact of their work on various scientific and engineering disciplines.
“This work represents a significant step towards integrating bio-inspired sensors into complex computing scenarios,” concludes Lam. “Neuromorphic encryption using speckle events is at an early stage, yet its potential to transform information security and optical applications is profound.”
As the scientific community awaits further developments, the study sets a new benchmark in encryption methodologies, emphasizing the transformative power of interdisciplinary research in advancing data security in an interconnected world.
More information:
Shuo Zhu et al, Neuromorphic encryption: combining speckle correlography and event data for enhanced security, Advanced Photonics Nexus (2024). DOI: 10.1117/1.APN.3.5.056002
SPIE
Citation:
Event-driven optical encryption advances information security through neuromorphic imaging (2024, July 24)
retrieved 25 July 2024
from https://techxplore.com/news/2024-07-event-driven-optical-encryption-advances.html
This document is subject to copyright. Apart from any fair dealing for the purpose of private study or research, no
part may be reproduced without the written permission. The content is provided for information purposes only.
Comments are closed